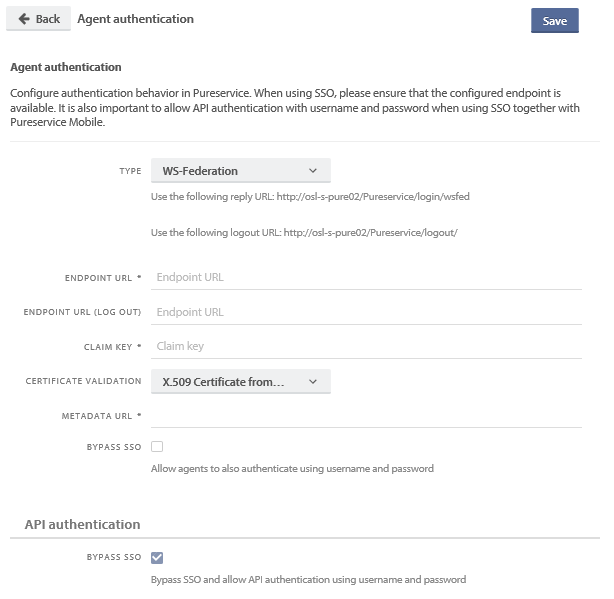
Configure Pureservice authentication with WS Federation
Configuring ADFS
- Open the AD FS Management console, expand “Trust Relationships” and select “Relying Party Trusts”
- In the actions list, select “Add Relying Party Trust..”
- Click start on the Welcome screen
- Select Data Source: “Enter data about the relying party manually” and click Next
- Specify Display Name: Can be anything, for example “Pureservice Trust”, then click Next
- Choose Profile: Select “AD FS Profile” and click Next
- Configure Certificate: Do not configure and click Next
- Configure URL: Select “Enable support for the WS-Federation Passive protocol”, enter the address for the WS-Federation endpoint (see examples below) and click Next
- Important! Must use HTTPS!
- Examples: https://YOUR-PURESERVICE-URL/login/wsfed/ / https://YOUR-PURESERVICE-URL/agent/login/wsfed/
- Configure Identifiers: Set the Pureservice site URL (example: https://YOUR-PURESERVICE-URL/agent/) and click Next
- Configure Multi-factor Authentication Now?: Select “I do not want to..” and click Next
- Choose Issuance Authorization Rules: Select “Permit all users to access the relying party” and click Next
- Ready to Add Trust: Click Next
- Finish: Choose “Open the Edit Claim Rules dialog..”
For ADFS to send the needed information to Pureservice, a “Claim Rule” must be set up that defines which attributes from Active Directory is mapped to the outgoing claims.
- Issue Transform Rules, right-click and select “Edit Claim Insurance Policy..”
- Select “Add Rule..”
- Choose Rule Type: Select “Send LDAP Attributes as Claims” (is selected by default) and click Next
- Configure Claim Rule
- Set a name, for example “Pureservice email/username from LDAP”
- Select Attribute Store “Active Directory”
- Set up Mapping
- This depends on what you want and your usernames in Pureservice
- Example: LDAP Attribute “SAM-Account-Name” -> Outgoing Claim Type “Windows account name” and/or LDAP Attribute “User-Principal-Name” -> Outgoing Claim Type “UPN”
Pureservice must be configured with an endpoint URL, Certificate information and which Claim key should be checked against the username.
Following is where this information can be found in ADFS. You will need this for later steps in the setup.
- Endpoint URL
- Open the AD FS Management console and expand “Service” -> “Endpoints” node
- Find the row with type “SAML-2.0/WS-Federation” and find the URL Path value
- Certificate #1
- Option 1: “X.509 Certificate from metadata URL” (in Pureservice): https://FEDERATIONSERVER/FederationMetadata/2007-06/FederationMetadata.xml
- Option 2: “X.509 Certificate” (in Pureservice): Open the XML document mentioned above (step 2a) and find the SignatureValue
- Certificate #2
- Open the AD FS Management console and expand “Service” -> “Certificates” node
- Find the “Token-signing” certificate and select “View Certificate..” in the Actions menu
- Choose “Details” in the certificate dialogue and find the values “Issuer” and “Thumbprint”
- Claim key
- Open the AD FS Management console and expand “Service” -> “Claim Descriptions” node
- Find the row that corresponds with the users’ usernames and find the Claim Type value
- The standard is http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress when email addresses are used as the usernames and http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn when UPNs are used as the usernames
- Important! Must correspond with the Claim Rule that was created in steps 1-4 for “Issue Transform Rules” in the previous section.
Configuring Pureservice
- Go to the Pureservice Agent Console and open the Administrator module, go to Security -> Authentication and select the relevant site (Agent authentication for the Agent Console and Enduser authentication for Selfservice)
- Choose Type: WS-Federation
- Endpoint URL: Enter the ADFS endpoint URL (step 1 in the previous section)
- Optional: Endpoint URL (Log out): Enter the URL if you want users to also be logged out of ADFS if using the log out function in Pureservice
- Claim key: Enter the relevant Claim key (step 4 in the previous section)
- Certificate validation: Select “Issuer name and thumbprint”, add the Issuer and Thumbprint in their separate fields (step 3 in the previous section)
- Optional: Enable Bypass SSO. This will allow users to log in “manually” with their Pureservice usernames and passwords while also having the option of using the WS-Federation Single SignOn.
- Save
Need more help with this?
Ta kontakt med oss for videre spørsmål her!