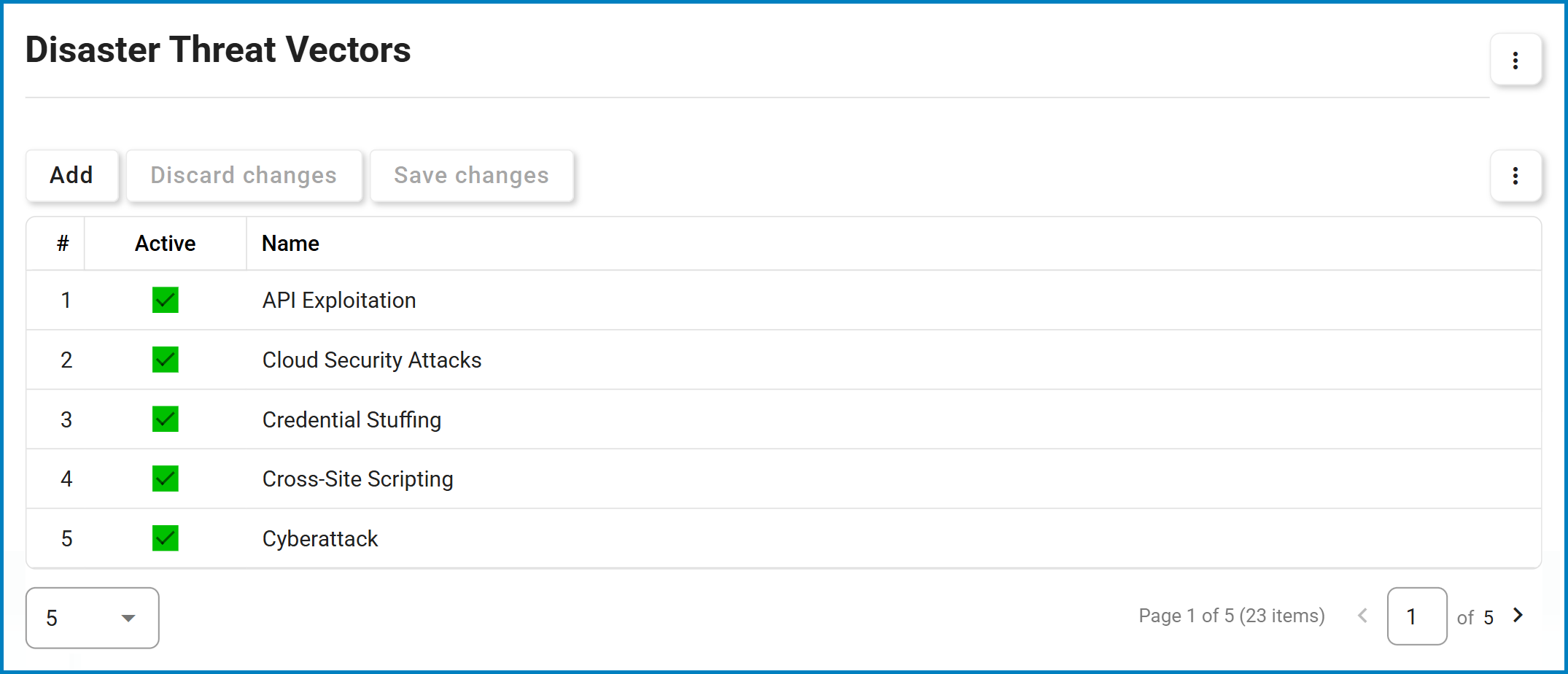
This module allows users to define and manage threat vectors, which are methods or pathways used to exploit vulnerabilities and disrupt operations.
Using the Module:
- Creating Threat Vectors
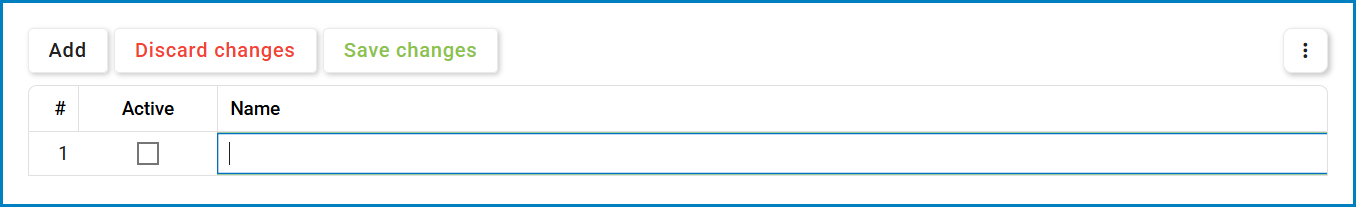
To add a new threat vector, click the Add button. A new row will appear in the grid, allowing users to enter the necessary details.
- Active: Check this box to mark the threat vector as active, or leave it unchecked to mark it as inactive.
- Name: Enter a descriptive name for the threat vector.
- Managing Threat Vectors
After adding a threat vector, users can perform the following actions:
- Editing Threat Vectors: Click directly in a grid cell to edit its contents.
- Saving & Discarding Changes
- Save Changes: Click the Save Changes button or click outside the grid to apply modifications.
- Discard Changes: Click the Discard Changes button to revert any unsaved modifications.



Post your comment on this topic.