Social Engineering
Social Engineering is a term that is widely used but the true meaning is not fully understood by most. It’s a type of information security attack that depends primarily on some type of human interaction. A hacker will often use some technical tools, such as phishing e-mails or fake websites to carry out this type of attack. But it’s the human interaction, an effort to prey on human weakness, that defines the attack as social engineering. In simple terms, social engineering means tricking or coercing people into revealing information or violating normal security practices.
Hackers will write viruses as a use of social engineering tactics to persuade people into opening e-mail attachments that are infected with malware. Scareware is also used which frightens people into running software that is useless but potentially dangerous to a computer system. Social Engineering mostly relies on the uneducated people of just how valuable their personal information may be to someone looking to steal it from their computer system.
Social Engineering has the same goals and objectives as other types of hacking: to gain unauthorized access, to commit identity theft, to infiltrate networks, or simply to disrupt communications or other operations. Targets can include anyone or anything that may have the information that the attacker may find valuable.
Email Analysis
After you have determined that a crime has been committed involving e-mail, first access the victim’s computer to recover the evidence. It might be necessary to log on to the e-mail service and access any protected or encrypted files or folders. If you can’t actually sit down at the victim’s computer, you may have to guide the victim on the phone to open and print a copy of an offending message, including the header. As we learned earlier, the header contains unique identifying numbers, such as the IP address of the server that sent the message. This information helps you trace the e-mail to the suspect.
Before you begin your analysis involving e-mail messages, it is best to copy and print the e-mail involved in the crime or policy violation. You might also want to consider forwarding the e-mail message as an attachment to another e-mail address as a backup. For many e-mail investigations, you can rely on e-mail message files, e-mail headers, and e-mail server log files However, if the e-mail administrator it’s willing to turn over records and files, or you encounter a highly customized e-mail environment, you can use data recovery tools and forensics tools designed to recover e-mail files.
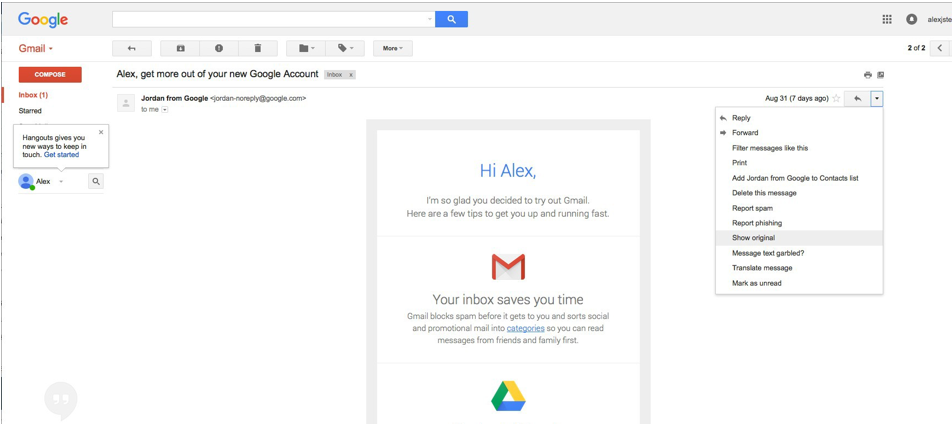
Examining Email Headers in Gmail
To examine an e-mail header in Gmail. Open the email message you wish to view the header. In to top right corner, click the drop-down arrow to reveal the menu options. Next, click on Show original. This will open a new window where you will be displayed with the header information of the email message.
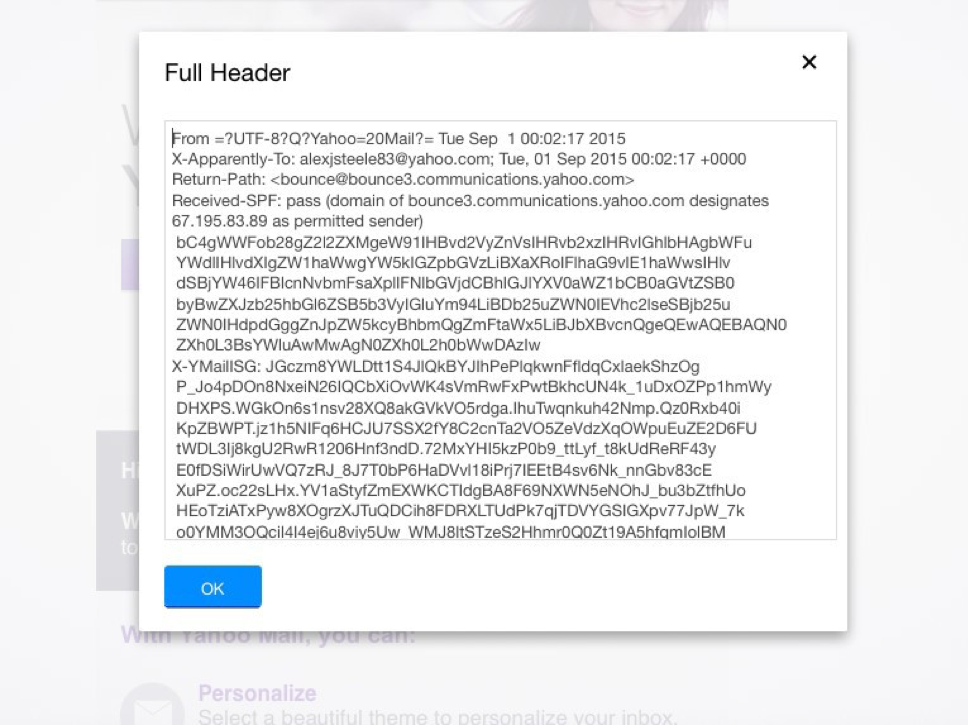
Examining Email Headers in Yahoo Mail
To examine an e-mail header in yahoo. Open the e-mail message you wish to view the header. In the top menu bar, click on More to reveal the menu options. Next, click on View Full Header. This will open a pop-up box revealing the full header of the email message. During our initial analysis at the time of this writing, there was not a way to resize this box, therefore, we suggest highlighting the next inside this box and copy and paste the header information into a notepad for better review.

Examining Email Headers in AOL Mail
To examine email header information in AOL mail, once signed into the AOL account, click on Settings icon, then click on Mail Settings, next click on Advanced and under the “When reading mail in Full view” click on these options: Always minimize headers, always minimize headers when I scroll, never minimize headers. And then click Save.



Post your comment on this topic.