There are several properties related to SAML authentication that will need to be added to the Orchid Fusion VMS configuration file. So as a first step, get the configuration file ready for these new settings. You won’t be able to fully configure the last three properties until you have configured your Identity Provider (IdP) (which will be explained later).
- Open the fusion.properties file.
- Add the following properties to the Orchid Fusion VMS configuration file:
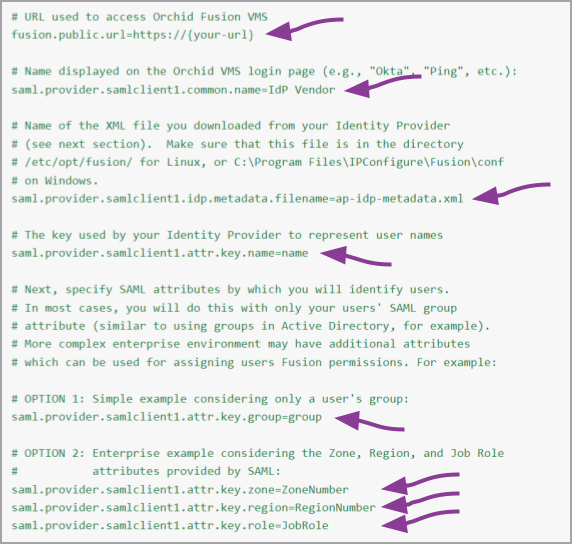
- fusion.public.url=https://your-url
- This is the public URL used to access your Orchid Fusion VMS.
- saml.common.setting.domain=yourdomain.com (This property is now obsolete and will be removed from the properties file upon upgrade.)
- saml.provider.samlclient1.common.name=IdP Vendor
- This is the provider name that will be displayed on the Orchid Fusion login page (such as Okta, Ping, etc.).
- saml.provider.samlclient1.idp.metadata.filename=ap-idp-metadata.xml
- This is the name of the XML file you will download from your IdP. (We’ll cover this in the next section.)
- If you’re working in Linux, this XML file must be placed in the following directory: /etc/opt/fusion/
- If you’re working in Windows, this XML file must be placed in the following directory: C:\Program Files\IPConfigure\Fusion\conf
- This is the name of the XML file you will download from your IdP. (We’ll cover this in the next section.)
- saml.provider.samlclient1.attr.key.name=name
- This is the key used by the IdP to identify a user.
- Add the following “group” property to the Orchid Fusion VMS configuration file to identify attributes in the external system to which Fusion will be able to map. You may configure multiple group properties which may include the standard group attribute, and/or any number of custom user attributes.
- saml.provider.samlclient1.attr.key.group=user-group
- For simple configurations, you may utilize the standard SAML group attribute, saml.provider.samlclient1.attr.key.group=group, which may be used to map the entire group of users to a Permission Group in Fusion.
AND/OR…
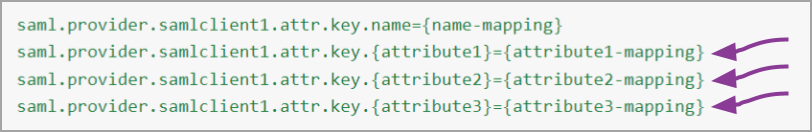
saml.provider.samlclient1.attr.key.<group attribute name>=<attribute-mapping>
Beginning in version 24.6.1, you may use multiple attributes to identify and assign external users to a Permission Group in Fusion.
In the following example, attribute1, attribute2 and attribute3 represent the property names we’ve defined in the Fusion properties file. The attribute1-mapping, attribute2-mapping and attribute3-mapping elements represent attributes that have been defined in the external system.
- Save changes to the properties file. (Don’t restart the Fusion service yet. We need to fill in more information first.)
Here’s what the SAML portion of your Fusion configuration file might look like at this point:


Post your comment on this topic.