Once your Orchid Fusion VMS properties file and Identity Provider web interface have been configured, you need to assign Fusion permissions for each of the groups you created within the IdP.
Beginning in version 24.6.1, SAML users may be mapped to a Permission Group using multiple attributes. (These attributes are identifiers that have already been assigned within the external IdP, such as Google or Ping.)
- With SAML fully configured, restart the Orchid Fusion VMS service.
- Now you need to associate your Orchid Fusion VMS Permissions Groups with the Identity Provider’s groups.
- Log into Fusion as an Administrator.
- Go to the Permission Groups screen. For each of your IdP groups that need to log into Fusion, do the following:
- Click the Add Permission Group button. (You may add these new groups to an existing Permission Group instead, if desired.)
- Enter a name and description for the new group.
- Go to the External Group Mappings tab.
- Check the Attribute Group Mappings section; it should display the external SAML group (or groups) that you have configured. (If your SAML group does not appear, there must be a problem with the SAML configuration. The configuration may be incomplete or inaccurate, or you may have forgotten to restart the Fusion service.)
- Click on the SAML group to expand it.
- Click the Create an Attribute Set button.
- Click the Attribute drop-down list to select an available attribute.
- In the Attribute Value field, enter the attribute value that is associated with your target users. (All of the users that match the attribute and value will be added as members of this Permission Group.)
- Click the Add Another Attribute button if you want to select another attribute. (If your Attribute Set contains multiple attributes, a user must match all of those attributes in order to be added to the Permission Group.)
- Click the Add an Attribute Set button if you need to incorporate users that have an entirely different group of attributes. (If you are using multiple Attribute Sets, a user must match at least one of those sets in order to be added to the Permission Group.)
- Use the Domain Group Mappings section if you need to add users from external systems outside of SAML.
- Use the remaining tabs to grant and revoke abilities and access, as needed.
- Click the Save Group button to save the Permission Group.
In the following example, we have a simple Permission Group that provides access to users in the orchid-hybrid-viewers SAML group. (In this case, that’s the name of a Google Workspace group):
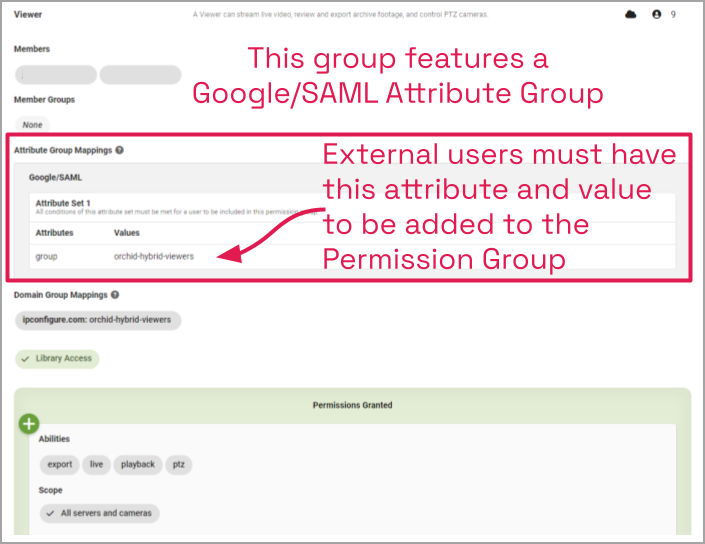
For additional details on adding external Permission Groups, please refer to the Orchid Fusion/Hybrid Administrator Guide.


Post your comment on this topic.